Provisioning Failures Detected Enter Cloudflare Credentials to Try Again
Integration with GlobalSign SSL
Key Manager Plus facilitates integration with GlobalSign signing say-so, making it possible for enterprises to automate the cease-to-end management of web server certificates signed and issued by GlobalSign from a centralized platform. This certificate discusses the steps to manage the life cycle operations of SSL/TLS certificates issued by GlobalSign direct from the Key Manager Plus web interface—right from importing existing orders, certificate request and provisioning, to deployment, renewal and thereupon.
Earlier y'all proceed with the integration, complete the post-obit step as a prerequisite:
Prerequisite
Add the following base URL and port equally an exception in your firewall or proxy to ensure Fundamental Managing director Plus is able to connect to the GlobalSign'due south CA Services.
URL: https://system.globalsign.com/kb/ws/v1
Port: 443
- Steps to Add GlobalSign Account into Key Manager Plus
- Place a Certificate Order
- Domain Control Validation, Certificate Issue & Deployment
- Renew, Reissue, Verify & Delete
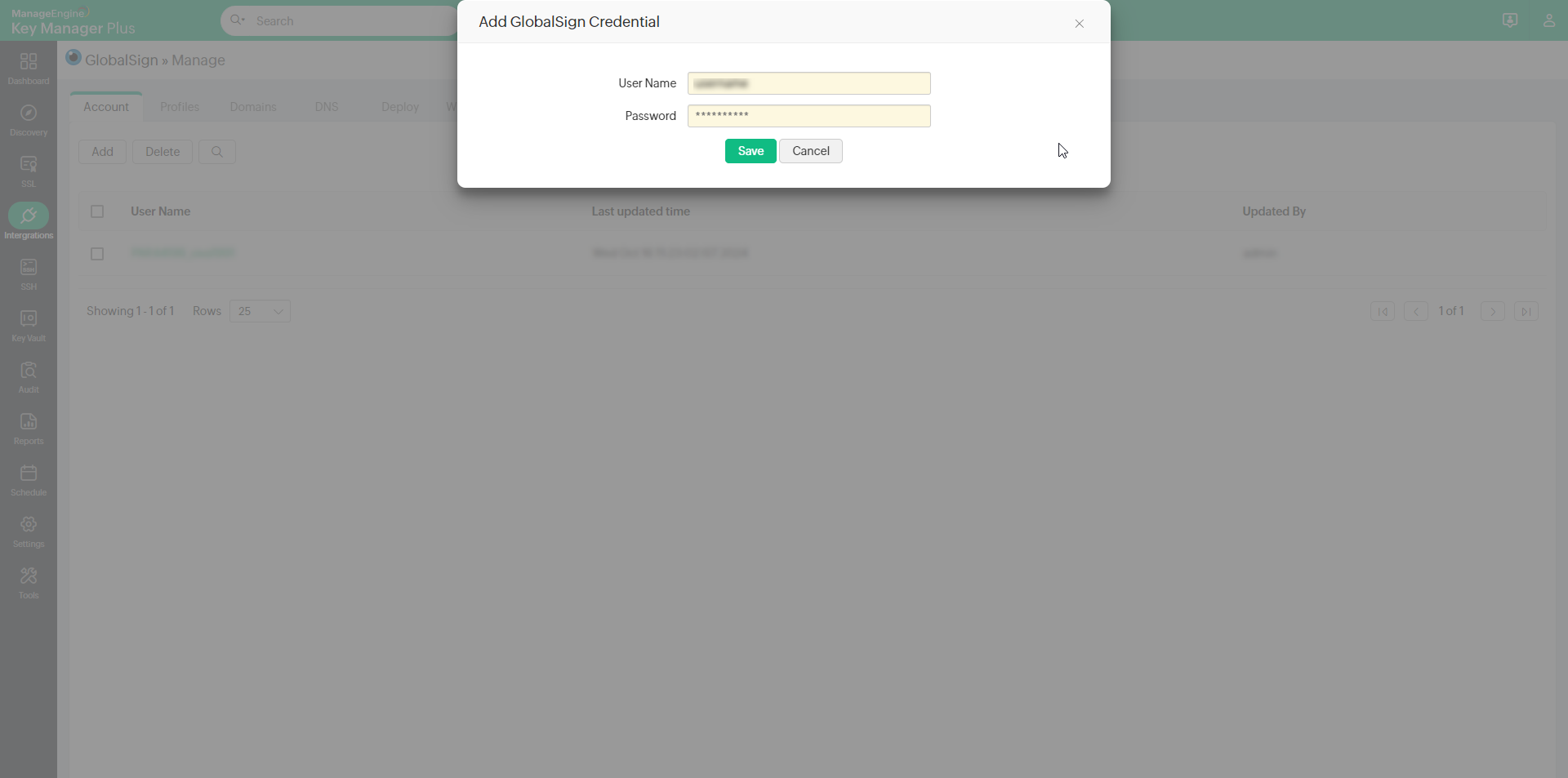
1. Steps to Add GlobalSign Account into Key Director Plus
Follow the below steps to add your GlobalSign account into Key Manager Plus:
- Navigate to SSL >> GlobalSign and enter your GlobalSign credentials for authentication.
- Once your GlobalSign account is verified and added, you may go on with the below steps.
- If the GlobalSign business relationship fails to get added to Fundamental Director Plus, contact the GlobalSign support, go an exception for the user'south IP address and try again.
- In case of account add failure, the IP address volition be available in the Audit section.
two. Place a Certificate Club
Once you take configured your GlobalSign credentials, you lot can at present leverage GlobalSign's API to generate certificate signing requests (CSRs), place orders, procure, and manage certificates direct from Key Manager Plus.
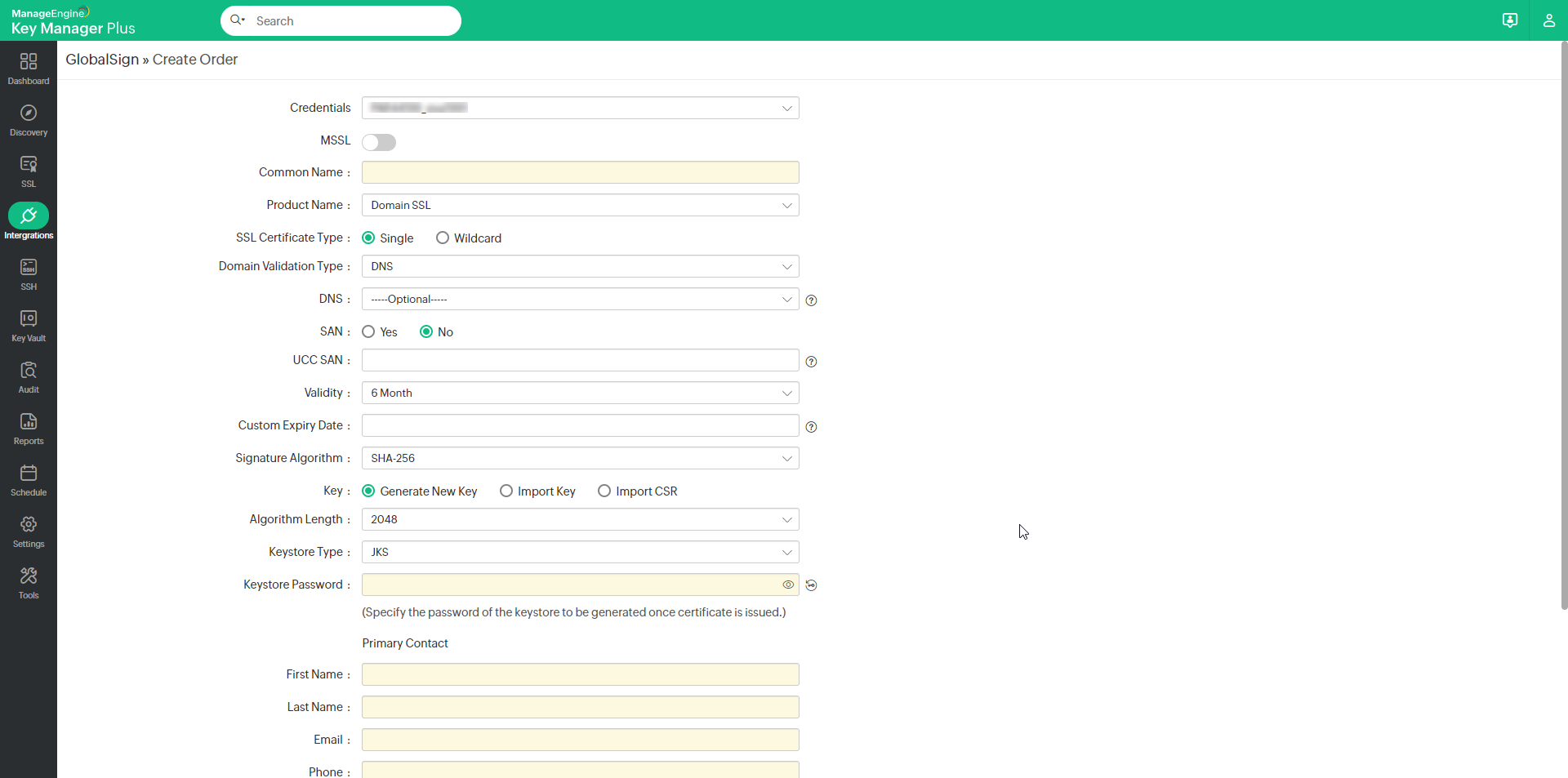
To generate a CSR and place a certificate club,
- Navigate to the SSL tab >> GlobalSign.
- Click Order Document.
- In the window that opens, enter the Common Name, Product Name, SSL Certificate Type, Domain Validation type and Validity.
- Key Manager Plus supports all the three domain control validation methods: DNS-based, file-based and e-mail validation.
- Then provide the SSL certificate blazon, signature algorithm, algorithm length, keystore blazon, keystore password, main and secondary contact details. Users likewise have the selection to import and utilise an already existing CSR or private key.
- If the Product Proper noun is called as Domain SSL, enter the SSL Document Type as Single/Wildcard.
- For any Product Proper name other than Domain SSL, provide the UCC SAN and validity for the same.
- The approver email ID is the email ID to which Domain Control Validation (DCV) verification post will be sent. The approver email ID should take either of the following formats:
- <admin@domain>, <administrator@domain>, <hostmaster@domain>, <webmaster@domain> or <postmaster@domain>
- Whatsoever administrator, registrant, tech or zone contact electronic mail address that appears on the domain's WHOIS record and is visible to the CA system.
- Then, provide the organization details(applicative for organization validation and extended validation order types but), administrator contact details and contact details of the technician placing the certificate society.
- Subsequently filling in the details, click Create.
- You will be taken to a window where you lot tin can encounter the listing of certificate orders placed along with their statuses displayed to the correct of the table view.
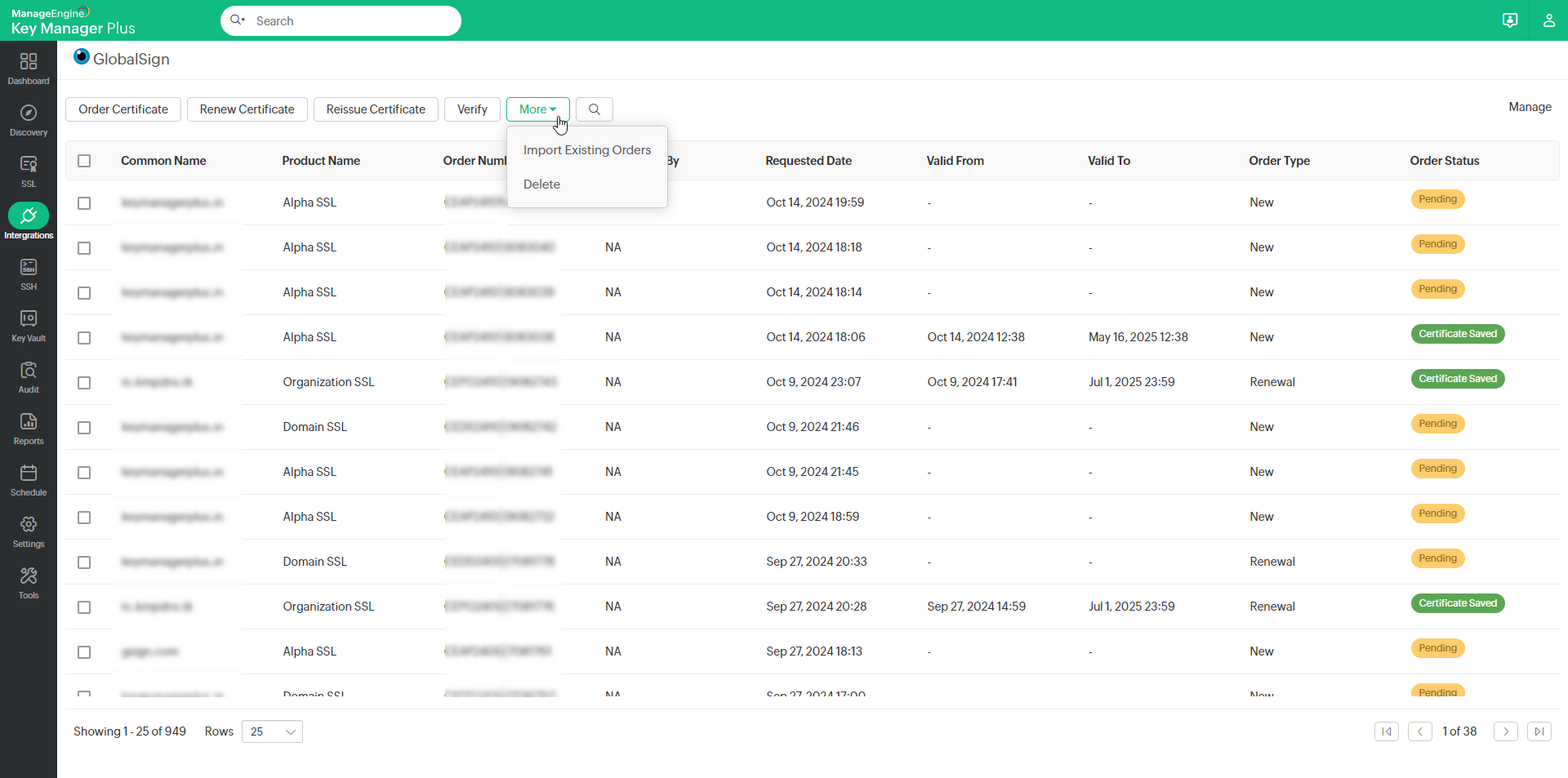
Note:Key Manager Plus allows you lot to import the already existing certificate orders placed within your account from GlobalSign and rails their statuses. Click Import Existing Orders from the More than tiptop card to import the existing open up orders into Key Manager Plus.
2.one Configuring your DNS Account
If yous are opting for DNS based domain validation in the certificate order, you should configure the DNS account in Key Manager Plus and specify it in the 'DNS' field in the order for automating the challenge verification procedure. To configure your DNS account,
- Navigate to GlobalSign >> Manage
- Switch to the DNS tab.
- Here, y'all can add a maximum of one DNS account for each DNS provider supported. Fundamental Director Plus currently supports automatic domain control validation for Azure, Cloudflare, Amazon Route 53 DNS, RFC2136 DNS update, GoDaddy DNS, and ClouDNS.
- Click Add. In the popular-upwards that opens, choose the DNS provider.
2.1.one Azure DNS
- Provide the Subscription ID, which is available in the Overview page of the Azure DNS zone.
- Provide the Directory ID, which is available in Azure Active Directory → Properties.
- If you have an already existing Azure application, provide its Application ID and Key.
- If non, follow the steps mentioned in this document to create the Azure awarding and key, and give the application access to the DNS zones for making API calls.
- Finally, enter the Resource Group Proper noun, which is the group name in which y'all accept created the DNS zone and click Save.
- Your DNS account details are saved and listed nether Manage >> DNS.
2.1.2 Cloudflare DNS
- In the Email address field, specify the e-mail address associated with the Cloudflare business relationship.
- For Global API Fundamental, use the 'Generate API' central option in the domain overview page of the Cloudflare DNS to generate the key and paste the value in this field.
- Click Relieve. Your DNS account details are saved and listed nether Manage >> DNS.
Note:For DNS based domain validation type, if you are going to specify an already configured DNS account in the certificate social club for domain command validation, brand certain its condition is marked Enabled under Manage >> DNS.
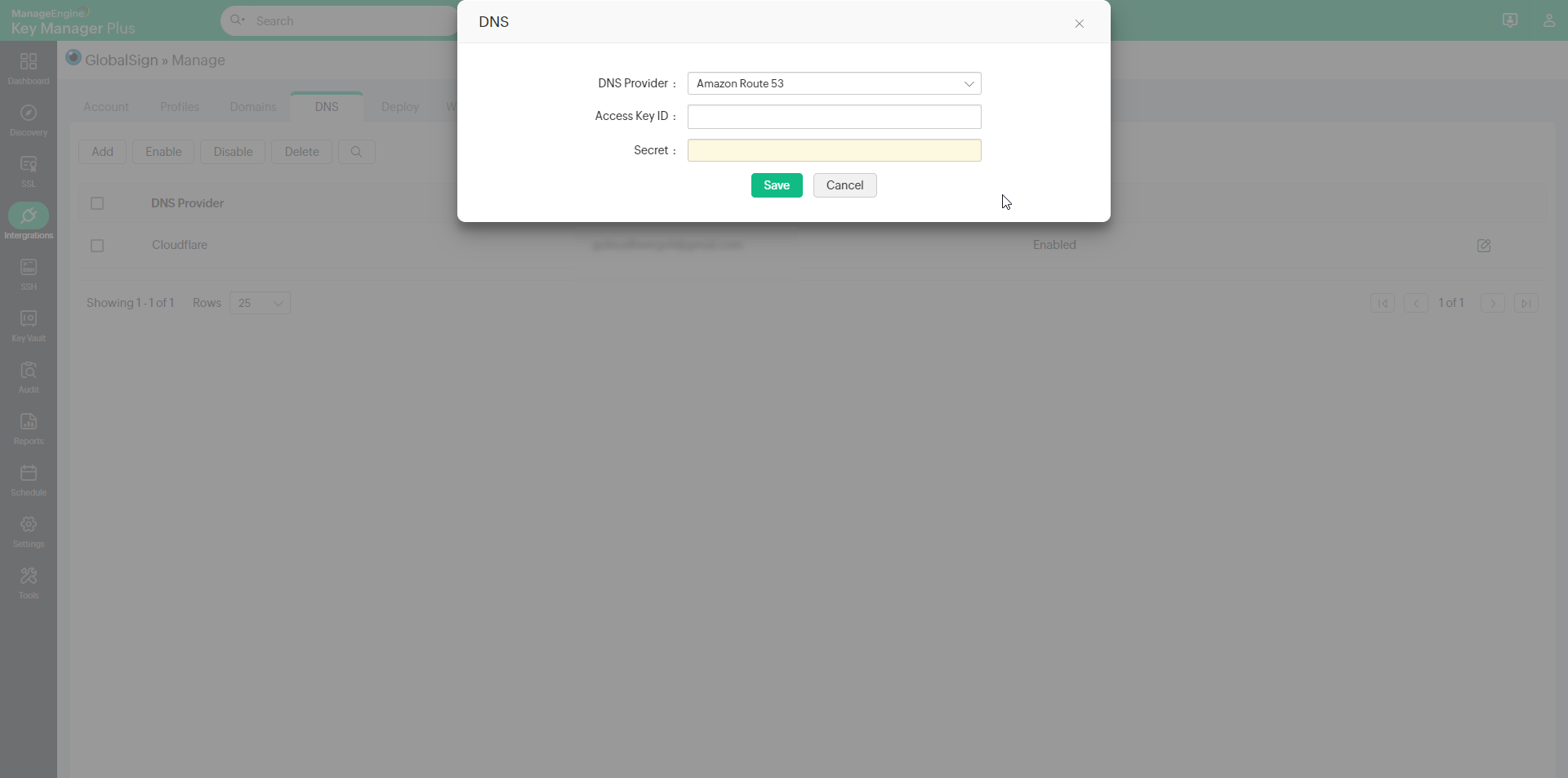
2.1.3 AWS Route 53 DNS
- Generate and specify the Access Cardinal ID and Secret associated with your AWS account.
- If you lot practice not accept an AWS account, create one and generate the Access Key ID and Clandestine by post-obit the steps given below:
- Login to the AWS console and navigate to IAM Services >> Users.
- Click Add user.
- Provide the user name and select the access type every bit Programmatic admission.
- Switch to the next tab, click Adhere existing policies directly under Prepare Permissions and search for "AmazonRoute53FullAccess".
- Assign the policy that is listed and switch to the adjacent tab.
- In the tags section, add appropriate tags (optional) and switch to the next tab.
- Review all the information entered and click Create user.
- The user account is created and afterward, an access fundamental ID and a hole-and-corner is generated. Copy and salve the primal ID and underground in a secure location for information technology volition not exist displayed again.
- If you already have an AWS user account, you accept to grant "AmazonRoute53FullAccess" permission to the user and generate the access fundamental if the user doesn't have ane. And if the user account has an access key associated already, it is just enough to ensure the required permission is granted.
To grant the required permissions, follow the below steps:
- Navigate to the Permissions tab, select the required user business relationship and click Add Permission.
- Click Attach existing policies directly under Ready Permissions and search for "AmazonRoute53FullAccess".
- Assign the listed policy and hit Save.
- To generate the access key,
- Select the particular user account and navigate to the Security Credentials tab.
- In the window that opens, click Create access key.
- An access key ID and a cloak-and-dagger is generated. Re-create and relieve the central ID and secret in a secure location for information technology will not be displayed again.
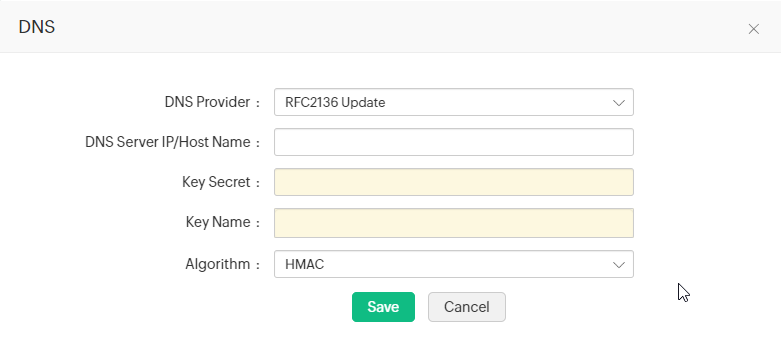
two.1.4 RFC2136 DNS Update
If you are using open source DNS servers such as Demark, PowerDNS etc., that back up RFC2136 DNS update, follow the steps below to automate DNS-based domain control validation procedure using Central Manager Plus.
- The DNS Server IP / Hostname represents the server name / IP address in which the DNS server is installed or running.
- These details are unremarkably establish in the server installation directory. For example, in the instance of Bind9 DNS server, you can find these in the filenamed.local.conf in the server installation directory.
- Provide the Cardinal Secret, which is nix but the key content constitute in the server installation directory.
- Provide a name for the primal, and choose the signature algorithm.
- ClickSave.
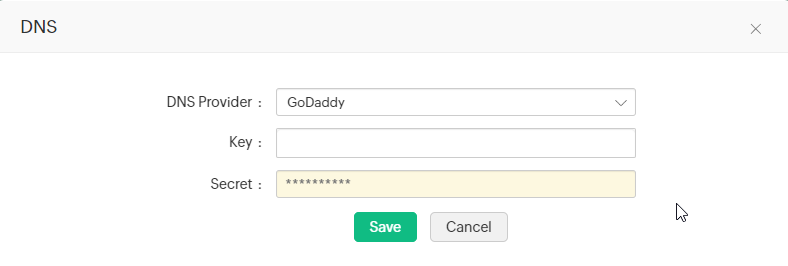
ii.one.5 GoDaddy DNS
If yous are using GoDaddy DNS for DNS validation, follow the steps below to automate DNS-based domain control validation procedure using Primal Manager Plus:
Steps to Obtain GoDaddy API Credentials:
- Go to the GoDaddy developer portal and switch to theAPI keys tab.
- Log in to your GoDaddy business relationship if you aren't logged in already.
- Once you lot log in, you will exist redirected to the API keys folio where you can create and manage API keys.
- Click Create New API cardinal.
- Provide your application name, cull the environment type every bitProduct and clickNext.
- The API fundamental and its hush-hush is generated. Re-create and salvage the surreptitious in a secure location, as it will not be displayed again.
Now, in Key Manager Plus interface, follow the below steps to add GoDaddy DNS to GlobalSign CA:
- Navigate toSSL >> GlobalSign and clickManage from the right almost corner.
- Switch to theDNS tab and clickAdd.
- ChooseGoDaddy from the DNS Provider driblet-down carte.
- Enter theKey andSecret that was previously generated from the GoDaddy portal.
- ClickSave.
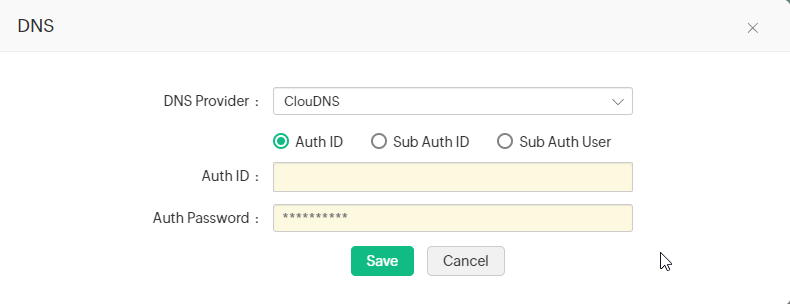
2.one.6 ClouDNS
If you are using ClouDNS for DNS validation, follow the steps below to automate the DNS-based domain control validation procedure using Key Manager Plus:
Steps to Obtain ClouDNS API Credentials:
-
Login to your ClouDNS account and go to Reseller API.
-
If you lot accept already created an API user id, you will find information technology under API Users. If non, click Create API to generate a new one.
Click here to learn more about ClouDNS API Auth IDs.
Now, in the Cardinal Manager Plus interface, follow the below steps to add ClouDNS to GlobalSign CA:
- Navigate toSSL >> GlobalSignand clickManage from the correct most corner.
- Switch to theDNS tab and clickAdd.
- Cull ClouDNSfrom the DNS Provider drop-down.
-
Choose one of the post-obit options: Auth ID, Sub Auth ID, Sub Auth User.
-
Enter the called ClouDNS Auth ID, its corresponding Auth Password, and click Relieve.
3. Domain Control Validation, Document Issue and Deployment
One time the document authority receives your order, you will have to go through a process called Domain control validation (DCV) and evidence your ownership over the domain upon the completion of which you lot volition receive the certificate. Key Manager Plus supports all the 3 DCV methods:
- E-mail based Domain Command Validation
- File or HTTP based Domain Control Validation
- DNS based Domain Command Validation
3.1 Electronic mail based Domain Control Validation
- In electronic mail based domain control validation, the certificate authorisation sends a verification electronic mail to the approver email ID specified when placing the certificate gild.
- This e-mail will guide you through the steps need to be performed in order to consummate the domain control validation procedure.
- After completing the steps, navigate to the Key Managing director Plus server, and switch to the GlobalSign tab.
- Select the lodge and click Verify from the top carte du jour.
- On successful verification, the document authority bug the certificate which is fetched and added to Key Manager Plus' secure repository. You can admission the certificate from the SSL >> Certificates tab.
- From here, you lot can deploy the certificate to necessary terminate-bespeak servers such equally a Certificate Store or an IIS server straight from Key Manager Plus.
Click hither for more details on certificate deployment.
iii.2 File / HTTP based Domain Control Validation
- If you have opted file / HTTP based domain control validation, a challenge file is displayed on creating the lodge.
- Navigate to the domain server, create the path specified and deploy the challenge file in that path.
This unabridged process of deploying the challenge file in the finish-indicate server tin can be automatic from Key Director Plus. This can be achieved by configuring the server details in the Deploy tab under Manage. To automate domain control validation,
- Switch to GlobalSign >> Manage.
- If the end-server is a Windows motorcar, initially download and install the Cardinal Managing director Plus agent for Windows server from the Windows Agents tab using the following steps
Installing Key Managing director Plus Agent for Windows Server:
To install Key Managing director Plus agent as a Windows service,
- Open up the command prompt and navigate to the Cardinal Managing director Plus installation directory.
- Execute the control 'AgentInstaller.exe start.'
To stop the agent and uninstall the Windows service,
- Open the command prompt and navigate to the Key Director Plus installation directory.
- Execute the command 'AgentInstaller.exe finish.'
- Switch to the Deploy tab and click Add.
- In the pop-upwards that opens, choose the challenge type as 'http-01' , specify the domain proper noun, cull the server type (Windows or Linux) and enter the server details. Click Salvage.
- The challenge file is automatically deployed to the corresponding finish-server in the specified path.
- In one case you lot accept deployed the challenge file, navigate to the Fundamental Manager Plus server, switch to the GlobalSign tab, cull the order and click Check Lodge Status from the tiptop menu.
- On successful domain validation, the certificate authorisation issues the certificate which is fetched, added to Cardinal Manager Plus' document repository (SSL >> Certificates).
3.3 DNS based Domain Control Validation
- If you have opted DNS based domain control validation, a DNS claiming value and text record are displayed on creating the gild.
- Copy and paste the text records manually in the domain server.
Like to the HTTP challenge, the entire challenge verification process can be automatic from Key Director Plus. This tin be achieved by configuring the server details in the Deploy tab nether Manage. To automate domain command validation,
- Switch to GlobalSign >> Manage.
- If the terminate-server is a Windows motorcar, initially download and install the Primal Manager Plus agent for Windows server from the Windows Agents tab using the steps mentioned in the previous section.
- Switch to the Deploy tab and click Add.
- In the pop-up that opens, choose the challenge type every bit 'dns-01', specify the domain name, choose the DNS provider (Azure, Cloudflare, Amazon Route 53 DNS, RFC2136 Update, GoDaddy, or ClouDNS) and enter the server details.
- Check 'Deploy Certificate' option to deploy the certificate to the cease-server afterwards procurement. Click Save.
- The DNS claiming values and text records are automatically created in the corresponding DNS servers.
- In one case the challenges have been fulfilled, navigate to the Primal Manager Plus server, switch to the GlobalSign tab, choose the lodge and click Check Society Status from the peak carte du jour.
- On successful domain validation, the certificate authority issues the document which is fetched and automatically added to Central Director Plus' certificate repository. You tin can access the document from the SSL >> Certificates tab.
- From here, you tin deploy the certificate to the necessary end-bespeak servers such every bit a Certificate Shop or an IIS server straight from Key Manager Plus. Click here for more than details on certificate deployment.
Notes:
- For DNS based domain control validation, if you had chosen a DNS business relationship configured under Manage >> DNS when placing the order, Key Manager Plus automates challenge verification using that account. Instead, if you have already configured the domain and server details under Manage >> Deploy, the claiming verification, and after the deployment of certificates is carried out for that specific domain and server lonely.
- For RFC2136 DNS update, if you have opted Global DNS configuration, the domain proper name itself acts as the zone name (Global DNS configuration is possible just if yous are using the aforementionedKey Cloak-and-dagger for all zones). Whereas, if you accept opted domain-agent mapping, you lot take to provide the Zone proper name, Cardinal Proper name, and Key Secret for each domain separately.
4. Renew, Reissue, Verify & Delete
You can renew, request reissue or delete certificate orders placed to third-political party certificate regime from Key Managing director Plus.
To renew a certificate:
- Navigate to SSL >> GlobalSign
- Select the required order and click Renew Certificate from the top menu.
- Complete the domain control validation (DCV) procedure if necessary.
- On successful validation, the document is issued and the new version is automatically updated in SSL >> Certificates tab.
Document renewal is allowed only 90 days before the death date of the selected certificate.
To request for a certificate reissue:
- Navigate toSSL >> GlobalSign
- Select the required order and clickReissue Certificatefrom the pinnacle carte.
- The certificate is reissued and automatically updated in the SSL >> Certificates tab.
To verify a certificate request:
- Navigate to SSL >> GlobalSign
- Select a certificate gild which is pending in Key Director Plus and click Verify from the top menu
- If the selected certificate is a Domain Validation document, then Primal Director Plus will perform Domain Verification and URL Verification with GlobalSign and upshot the certificate one time the verification is complete. The issued certificate will be added to the SSL certificate repository in Key Managing director Plus.
- If the selected certificate is not a Domain Validation certificate, then Key Manager Plus will fetch the status of the certificate alone from GlobalSign.
To delete a certificate asking:
- Navigate to SSL >> GlobalSign
- Select the required document and click Delete from the More than top bill of fare.
- The certificate request is deleted from Key Director Plus.
Note:When a certificate request is deleted, it is removed just from Key Manager Plus. You lot can find the order being open up in the GlobalSign website for your account and you tin can import it into Central Managing director Plus if needed usingGlobalSign >> More >> Import Existing Orders.
Source: https://www.manageengine.com/key-manager/help/globalsign-ssl-integration.html
0 Response to "Provisioning Failures Detected Enter Cloudflare Credentials to Try Again"
Post a Comment